Virtual MFA device for AWS accounts
It is best practice to secure your AWS (IAM or Root) user account with MFA, we can integrate AWS with Vault to achieve this. The TOTP secrets engine in Vault can be enabled and configured to be used as an MFA virtual device by AWS.
AWS can use Vault (TOTP Secrets Engine) for MFA, which enables us to not have a mobile device for each IAM user or root account that we want to protect with MFA (Multi-Factor Authentication).
TOTP stands for Time-based one-time passwords, and these are temporary passcodes which typically expire after a certain duration (30, 60, 120, or 240 seconds).
Solution Overview
An IAM/Root user will login using their appropriate credentials to an AWS account which has MFA enabled. Then the user will go to Vault to generate an MFA code for their account which will be validated by AWS.
Prerequisite
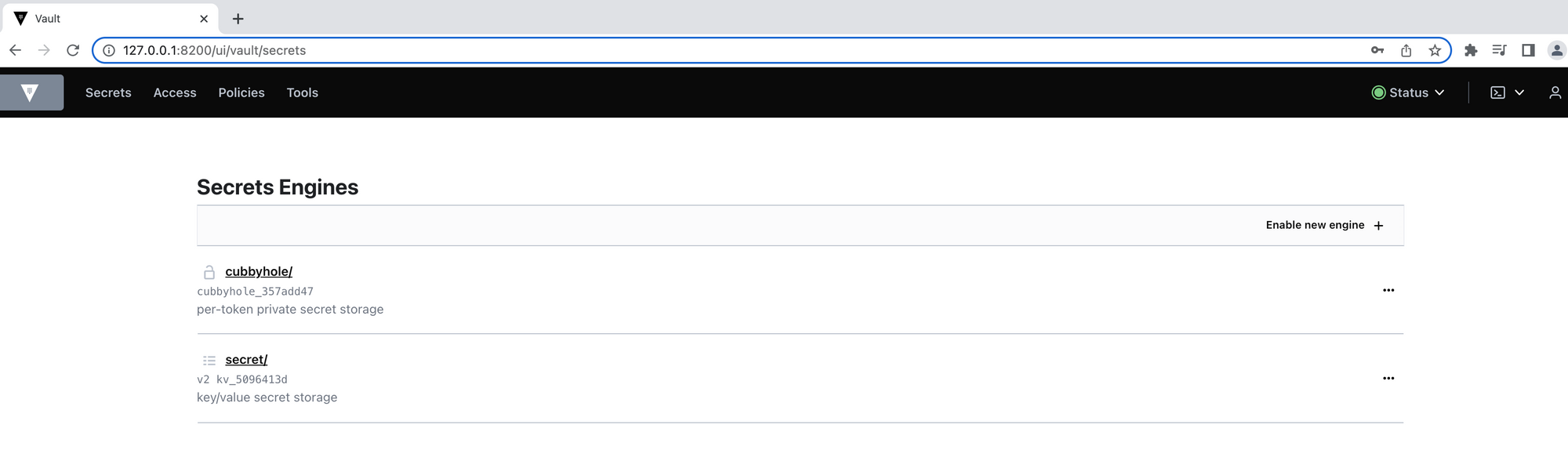
Ensure you have a running Vault node on your machine or in your AWS account like we did in the previous post. Below is the Vault UI with default secrets engines:
Step 1: Configure the TOTP Secrets Engine
The first thing we need to do is to setup the TOTP Secrets Engine for our Vault cluster.
- We can enable the engine on UI or via the terminal by running the command below:
vault secrets enable totp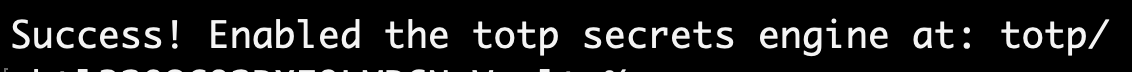
- Now we will go to the IAM Management Console to create a new user to use the TOTP secrets engine:
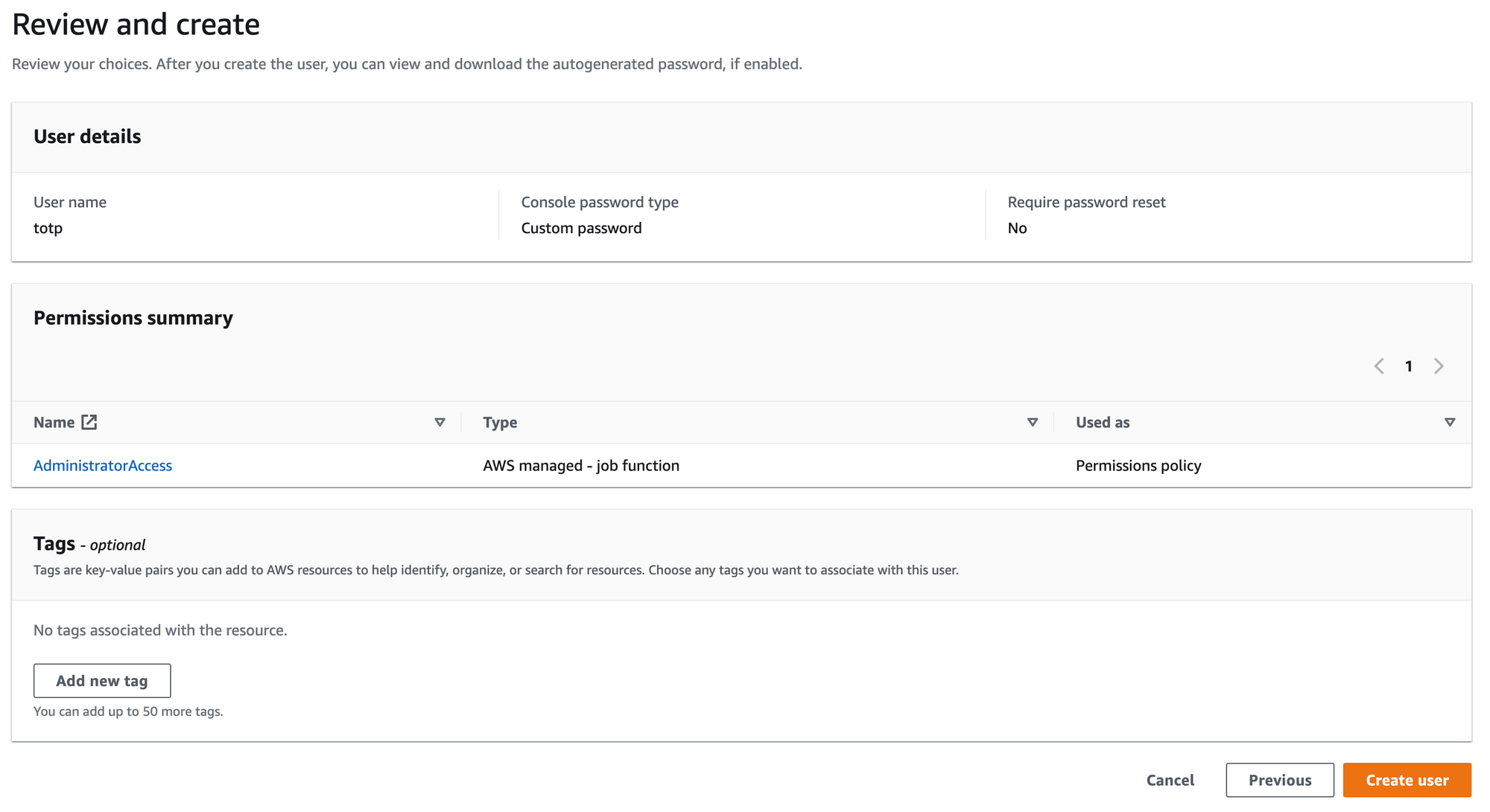
Step 2: Enable an MFA device for the user
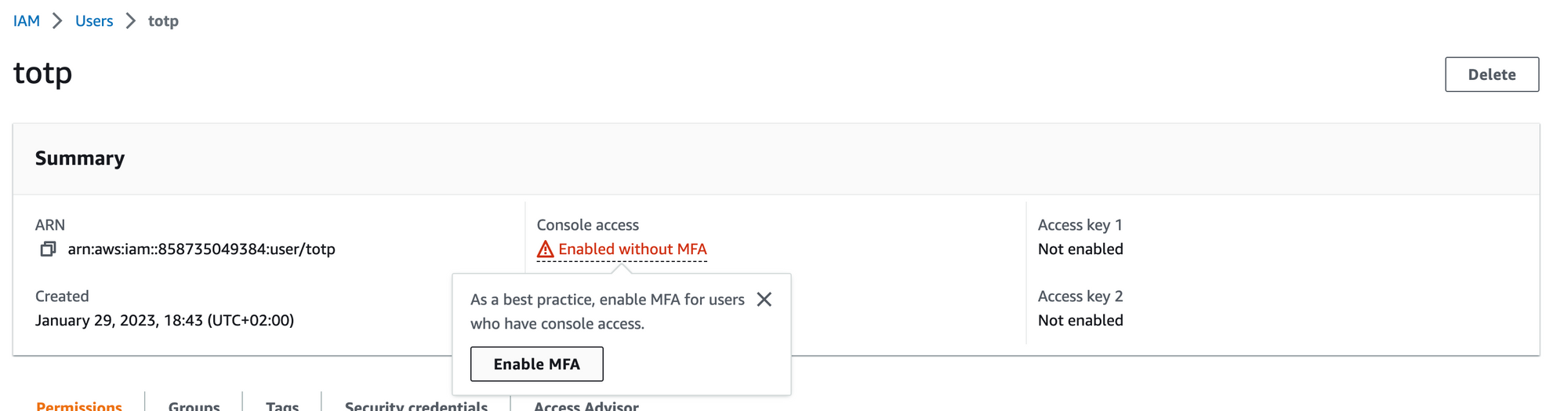
We now can go to the newly created totp user to assign an MFA device to secure the account.
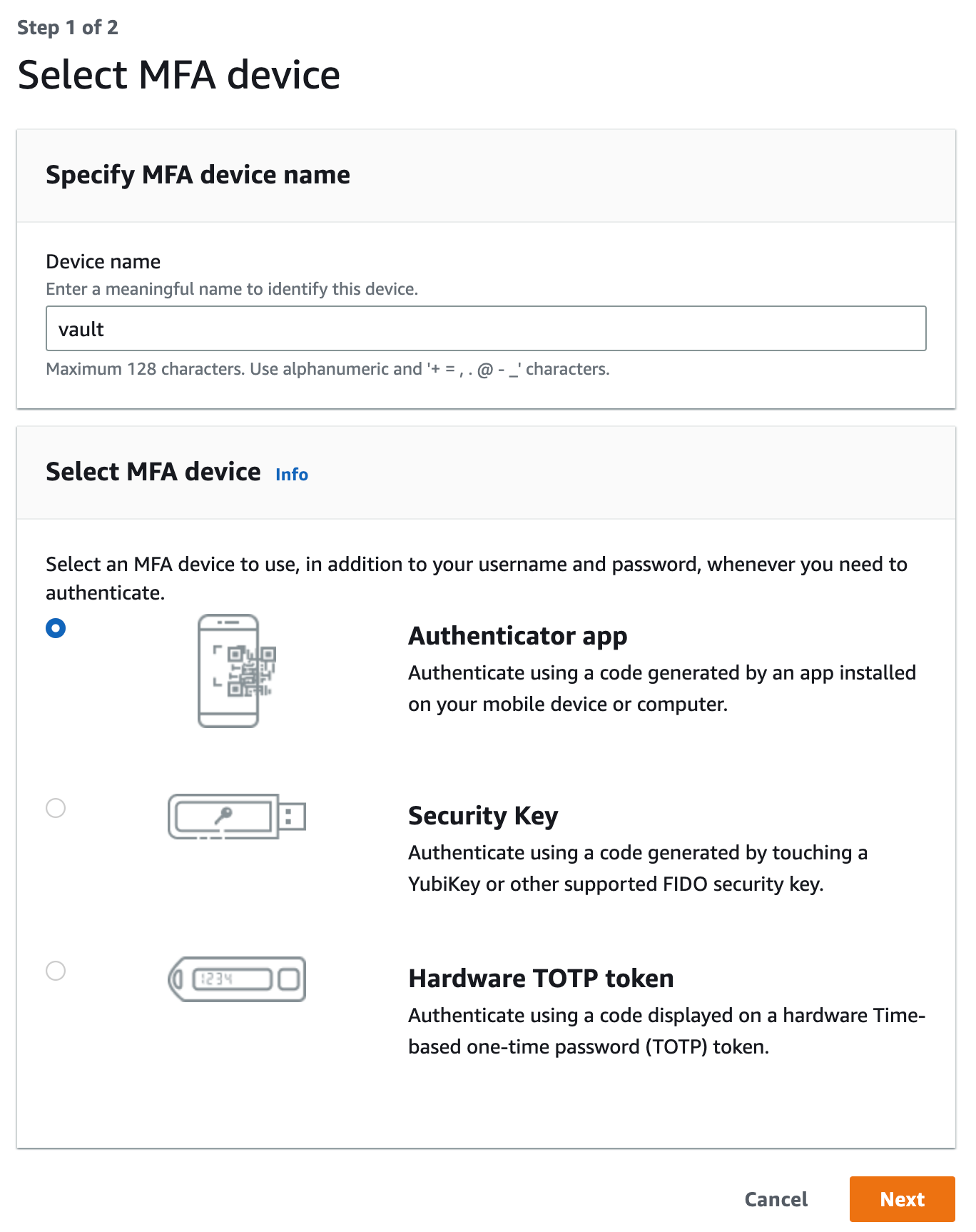
- We will name our virtual device
vaultand chooseAuthenticator appas our MFA device:
- Grab the secret key on the following page in order to generate the respective MFA code 1 and code 2 to finish setting up the virtual device:
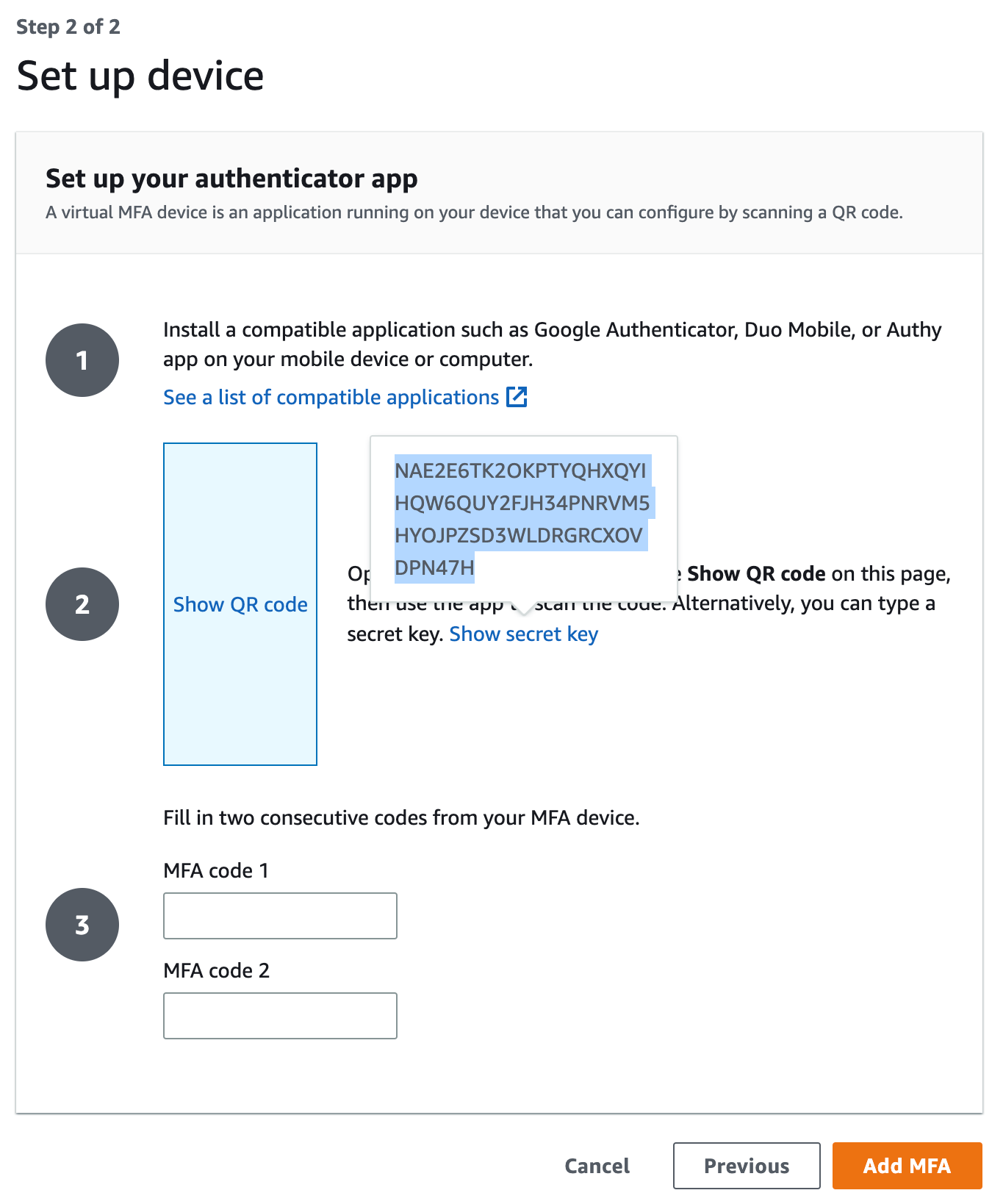
- We need to take note of our AWS account ID (e.g 858735049384) as well as the secret key (e.g NAE2E6TK2OK...) associated with the authenticator app. Configure a named key
awsby running the command below:
vault write totp/keys/aws \
url="otpauth://totp/Amazon%20Web%20Services:totp@858735049384?secret=NAE2E6TK2OKPTYQHXQYIHQW6QUY2FJH34PNRVM5HYOJPZSD3WLDRGRCXOVDPN47H"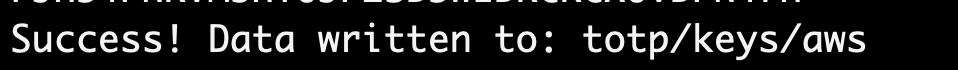
- We have written a new key, so we can finish setting up the MFA device by generating codes using the command below:
vault read totp/code/aws 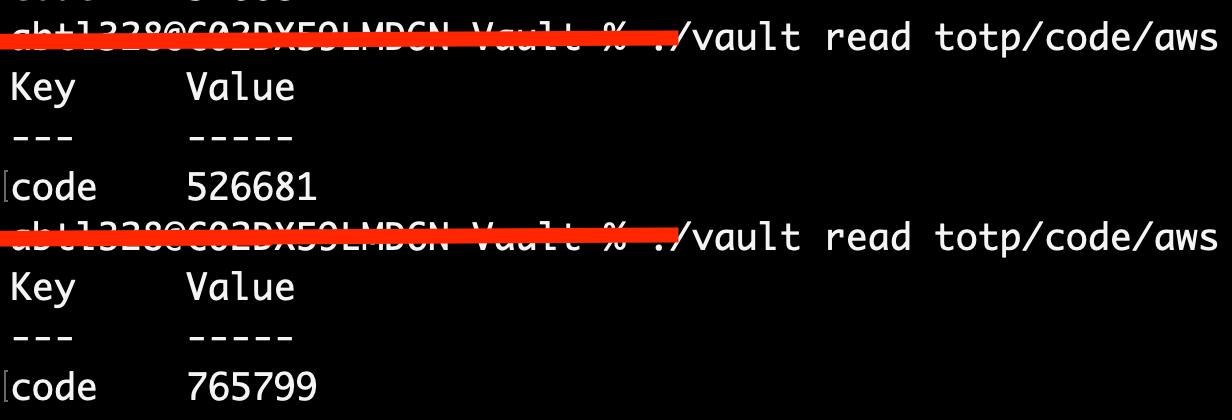
- We need to generate new time-based OTP by reading from the
/codeendpoint with the name of theawskey. We will use the generated keys to finish setting up the virtual device:
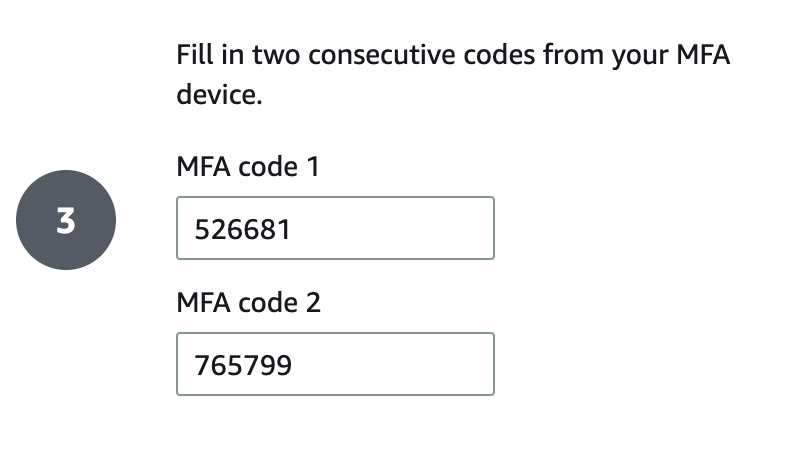
Step 3: Login using MFA
Since we have enabled MFA for the totp user in AWS, we can open a new incognito tab to test the setup
- We will login using the
totpuser we created in Step 1 with the passwordvaultTOTP!which will be deleted by the time you read this:
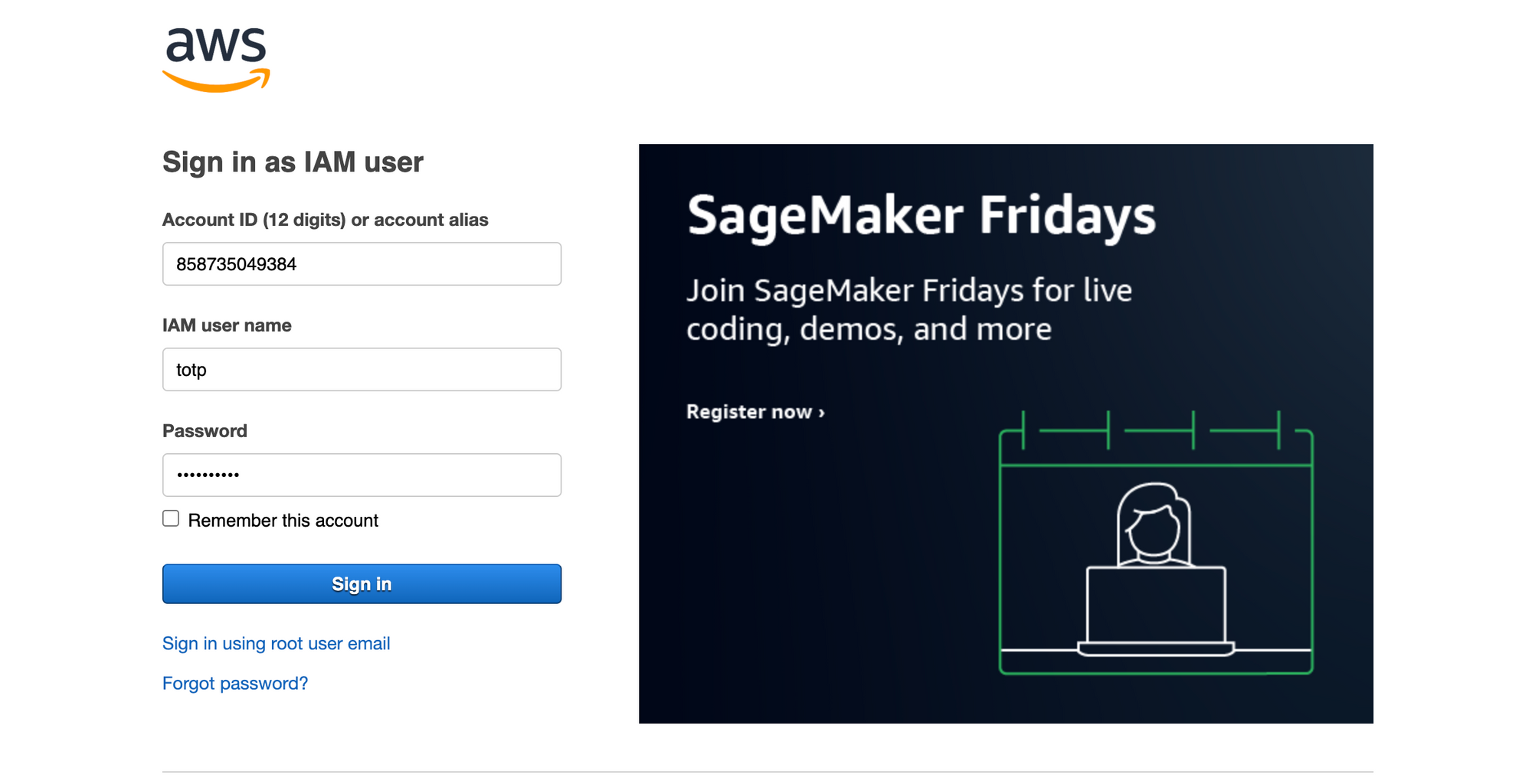
- Once we click
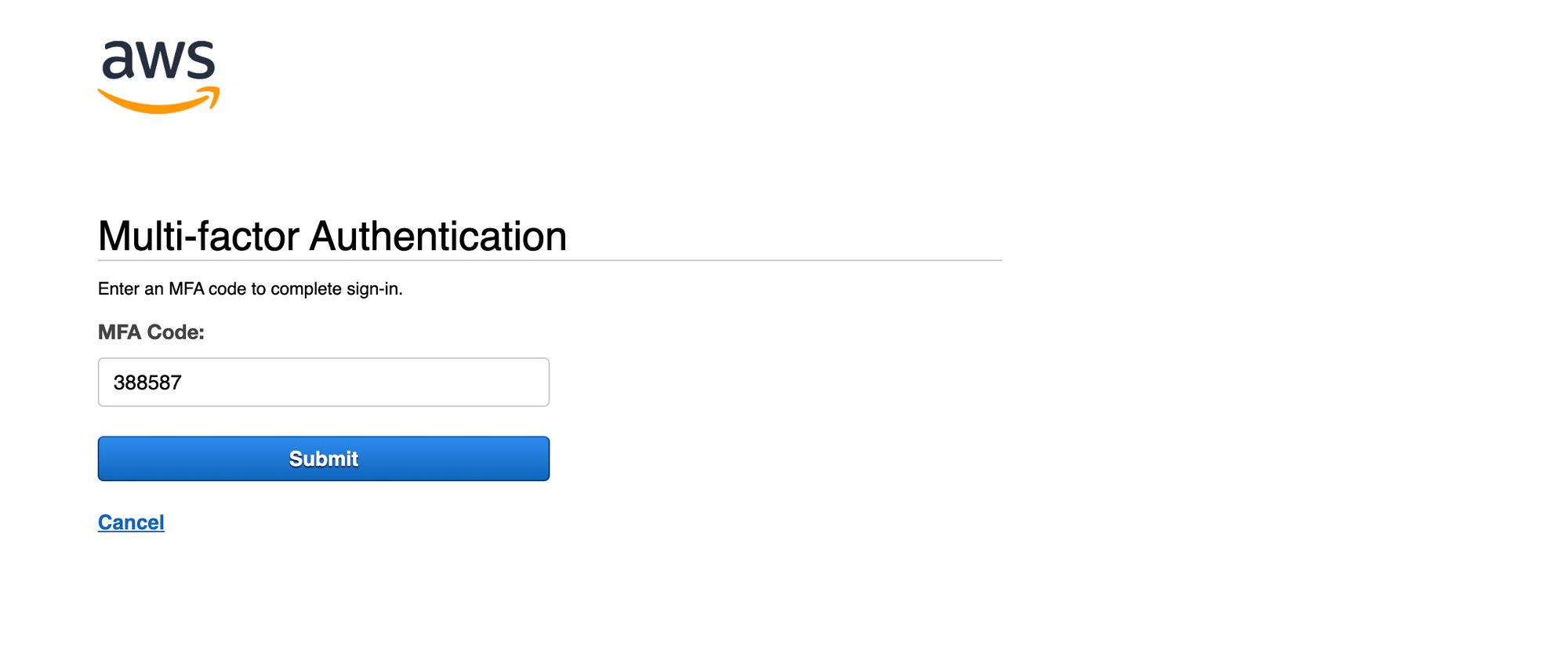
Sign inwe will be prompted to provide and MFA code to access the console. We need to run the command below to generate our code:
vault read totp/code/aws 
- Now that we have the code generated, we can provide it to AWS in orded to be fully authenticated:
Summary
Now we are using Vault as a virtual MFA for our IAM user in AWS, so our account is protected without having to use a mobile device or any physical device that can help with MFA. This is just another we can integrate Vault with AWS.